
Cybercriminals continue to rely on tried and tested tactics and old security weaknesses to exploit businesses, according to a new Threat Spotlight from Barracuda.
Taking in three months’ of detection data from the Intrusion Detection Systems (IDS) used by Barracuda’s Security Operations Center (SOC), part of Barracuda XDR, the data reveals how hackers were able to gain remote control of systems, install malware, steal information and more by using overlooked vulnerabilities and old tactics, some dating back 15 years.
Analysing the data, Barracuda researchers saw attackers using a 2008 tactic that would let them take advantage of a misconfigured web server to access sensitive operating system files to gain remote access to vulnerable systems.
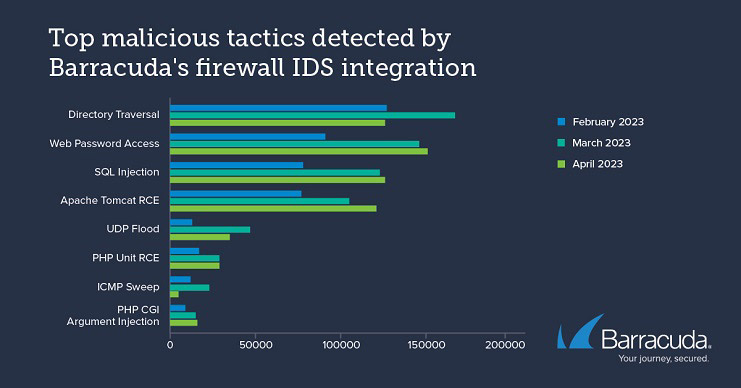
Other hackers achieved the same by using the 2003 tactic of injecting specially crafted malicious code into a legitimate process to allow them to read sensitive data, modify operations, and send instructions to the operating system.
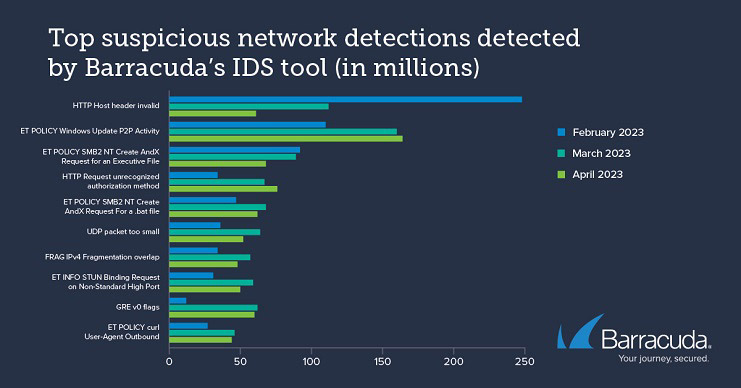
Attackers also acquired sensitive information by targeting vulnerable servers to obtain passwords and lists of users, or by misusing legitimate processes to find out how many computers on a network have an active IP connection. They also attempted to cause general chaos, disruption, and denial of service by messing with online traffic data packets, making them too small or fragmenting them so that the communications channels and destination servers become overwhelmed and crash.
“Security weaknesses don’t have a cut-off date, and the risk is that over time they can become harder to locate and mitigate, reduced to deeply embedded, shadow vulnerabilities in a system or application – and the tactics required to target them don’t need to be new or even sophisticated to succeed,” said Merium Khalid, senior SOC manager, offensive security, Barracuda XDR.
“A multi-layered approach to protection that has several levels of increasingly deep detection and scrutiny is essential. Knowing which vulnerabilities are hiding in your IT environment and who might be targeting them and how is vital – as is the ability to respond to and mitigate these threats.”






