The Threat
Cybercrime is a highly profitable and low risk business, which is why it’s costing the global economy more than $400 billion every year. Threats are continually evolving and scaling, making them harder and harder to detect and eradicate. The average time from infection to detection has been reported as being as high as 206 days, with a further 69 days being taken to eradicate the infection. So, what’s going wrong; why can’t the security industry combat this ever changing threat? A new buzz-term has emerged over recent months – security intelligence – coming with promises of quicker detection times and faster resolution times, at last putting our security teams on the front foot.
Let’s look at whether the promise of security intelligence is simply marketing hype or is there really a progressive paradigm shift happening in the security operations centres that finally sees our analysts getting ahead of the hackers.
The Challenge
For the past two decades, our beleaguered security analysts have been fighting what can only be described as a losing battle. Every day, billions upon billions of events flood from corporate servers, workstations, network devices and applications into our security operations centres’ systems. Every single event could be the trigger our analysts need to detect an attack and start the incident response process. However, correlating attack patterns and indicators of compromise (IOCs) from this kind of data deluge is an impossible task, and it’s often the more subtle, slow-burning attacks that go unnoticed.
Huntsman’s product development team has directly observed this issue within our customers’ security operations centres, seeing how even the best trained and most astute security analysts are getting burned out as they hunt for the proverbial IOC needle in the haystack of security events. Even the best, most experienced security teams can’t do everything they need to do to stay ahead of today’s ever-changing threat environment, which is why our customers have asked for help.
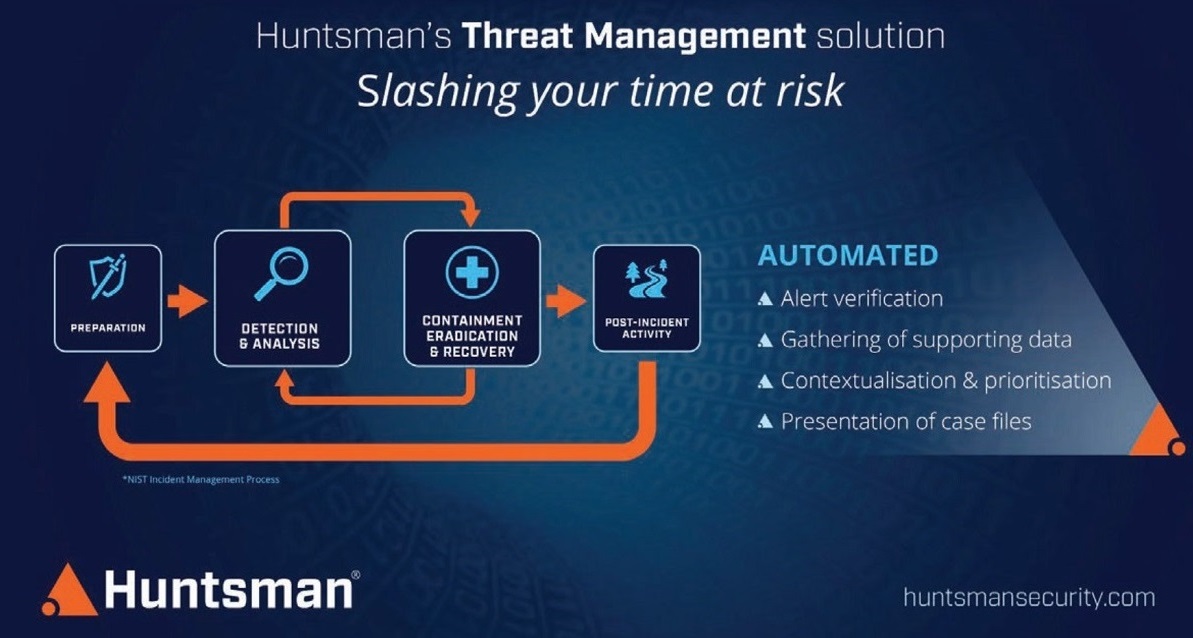
Automatic Threat Verification
Careful analysis of our customers’ security operations centres has shown that the biggest challenge modern security teams have is finding the time to do the truly valuable work they should be doing, such as hunting for cyber threats. The problem is that most investigations turn out to be nothing more than false alarms, triggered by misconfigured network devices, badly designed applications and miscommunicated system changes that create incidents, and can add up to weeks or even months of wasted effort every single year.
Forrester’s recent call to action suggests that the answer is in automation. “Businesses can no longer rely on passive, manual procedures to defend against attacks.” However, the challenge remains as to how we automate the detection of real attacks while filtering out events that relate to false positives, all the time guarding against anything that might be vital to our defence (false negatives). The answer comes in our ability to operate across the security value chain ensuring analytical completeness across the entire ‘kill chain’…Click HERE to find out more about this article





